Thermanator: Thermal Residue-Based Post Factum Attacks On Keyboard Password Entry
Thermanator is a post factum thermal imaging attack that allows an adversary recover full password key sets up to 30 seconds and partial password key sets up to 1 minute after password entry. The attack uses a mid-range thermal imaging camera.
Full paper available on arxiv.
Recent News
Thermanator was presented at the Black Hat Europe 2018. Abstract and presentation available.
Recent articles covering Black Hat Europe 2018 and our work:
"The best hacks from Black Hat Europe 2018", https://portswigger.net/daily-swig/the-best-hacks-from-black-hat-europe-2018
"14 Hot Sessions at Black Hat Europe 2018", https://www.bankinfosecurity.com/blogs/14-hot-sessions-at-black-hat-europe-2018-p-2691
Thermal Timelapse
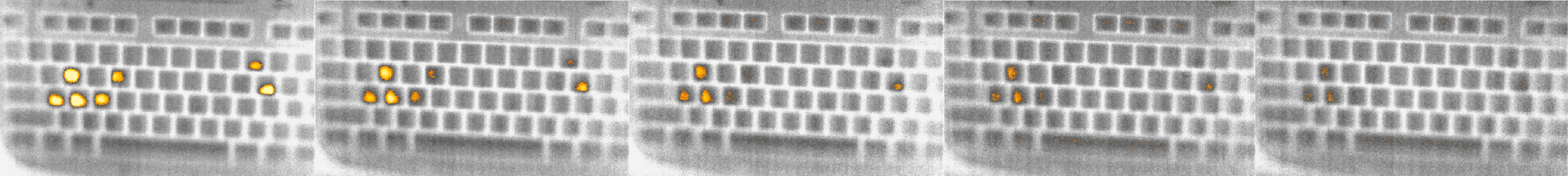
Password "passw0rd" thermal residue 0, 15,
30, 45 and 60 seconds after entry, left to right.
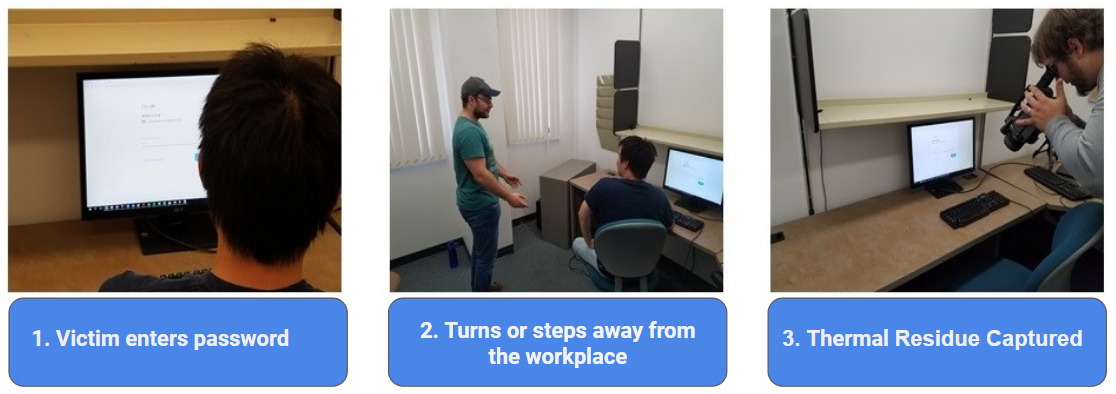
Example attack scenario
Authors
Tyler KaczmarekErcan Ozturk
Gene Tsudik
Media Coverage on AcuTherm: A Hybrid Attack on Password Entry Based on Both Acoustic and Thermal Side-Channels
-
AcuTherm was listed among 2-3 highlights of Black Hat Asia
https://www.blackhat.com/latestintel/03152019-dont-miss-intriguing-black-hat-asia-briefings.html
-
Articles in German press
https://www.heise.de/security/meldung/Seitenkanalattacken-Passwort-Klau-mittels-Waermebildkamera-und-Tippgeraeusch-4357232.html
https://www.golem.de/news/acutherm-mit-waermebildkamera-und-mikrofon-das-passwort-erraten-1904-140396.html
-
REDFOXNEWS.US
https://redfoxnews.us/dont-miss-these-intriguing-black-hat-asia-briefings/
-
DARKReading
https://www.darkreading.com/black-hat/dont-miss-these-intriguing-black-hat-asia-briefings/d/d-id/1334170
Media Coverage on Thermanator: Thermal Residue-Based Post Factum Attacks On Keyboard Password Entry
-
UC, Irvine ICS and CS
https://www.ics.uci.edu/community/news/view_news?id=1388
http://www.cs.uci.edu/ics-researchers-introduce-thermanator-revealing-a-new-threat-to-using-keyboards-to-enter-passwords-and-other-sensitive-information/
-
Schneier on Security
https://www.schneier.com/blog/archives/2018/07/recovering_keyb.html
-
THE TIMES
https://www.thetimes.co.uk/article/thermal-imaging-lets-hackers-read-what-you-ve-typed-cxmqtt3rm
-
DailyMail
http://www.dailymail.co.uk/sciencetech/article-5925865/Criminals-steal-bank-details-recording-HEAT-left-keyboard-fingers.html
-
BLEEPINGCOMPUTER
https://www.bleepingcomputer.com/news/security/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards/
-
Mirror
https://www.mirror.co.uk/tech/hackers-can-steal-your-computer-12858680
-
SECURITY BOULEVARD
https://securityboulevard.com/2018/07/thermanator-attack-uses-thermal-residue-from-keyboards-to-steal-your-passwords/
https://securityboulevard.com/2018/07/recovering-keyboard-inputs-through-thermal-imaging/
-
techradar
https://www.techradar.com/news/creative-keyboard-attack-allows-passwords-to-be-stolen-using-the-heat-from-your-fingers
-
GIZMODO
https://gizmodo.com/scientists-discover-hottest-most-improbable-way-to-ste-1827396066
-
ZDNet
https://www.zdnet.com/article/this-attack-steals-your-passwords-by-reading-keyboard-heat/
-
KSWO
http://www.kswo.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
-
TechRepublic
https://www.techrepublic.com/article/how-hackers-can-steal-your-password-with-an-infrared-photo-of-your-keyboard/
-
STORYPICK.
https://www.storypick.com/thermanator-cyber-attack-fingertips//
-
GBHackers
https://gbhackers.com/thermanator-attack-password-keyboards/
-
FOSSBYTES
https://fossbytes.com/keyboard-attack-thermanator-steal-password-using-body-heat/
-
welivesecurity
https://www.welivesecurity.com/2018/07/06/thermanator-attackers-heat-keyboard-password/
-
CYWARE
https://cyware.com/news/thermanator-hackers-could-steal-passwords-by-analyzing-thermal-residue-on-keyboards-df15f4c5
-
WFMJ
http://www.wfmj.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
-
THREAT BRIEF
https://threatbrief.com/this-keyboard-attack-steals-passwords-by-reading-heat-from-your-fingers/
-
WLOX
http://www.wlox.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
-
mycomputerlessons
https://mycomputerlessons.com/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards/
-
Academy Hacker
http://hackwolrdwide.com/thermanator-attack-attackers-can-steal-password-and-pins-typed-on-keyboards/tranning-it-hacking/2018/
-
MALWARETIPS
https://malwaretips.com/threads/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards-up-to-one-minute-after-input.84900/
-
SENSORS TECH FORUM
https://sensorstechforum.com/thermanator-thermal-residue-passwords/
-
Warehouse Discounts
https://warehousediscounts.co.uk/2018/07/this-keyboard-attack-steals-passwords-by-reading-heat-from-your-fingers/
-
JOURNALPOSTS
https://www.journalposts.com/new-insider-attack-steals-passwords-by-reading-thermal-energy-from-keyboards/
-
MogazNewsEn
https://en.mogaznews.com/Technology/958064/Criminals-can-steal-your-bank-details-by-recording-the-HEAT-left-on-a-keyboard-.html
-
LENTA.RU
https://lenta.ru/news/2018/07/05/fingers/
-
RTL.fr
https://www.rtl.fr/actu/futur/il-est-possible-de-voler-un-mot-de-passe-en-filmant-un-clavier-avec-une-camera-thermique-7794077571
-
iaftnews
https://traders-union.ru/iaftnews/kriptorinok/news/327373/
-
THE TIMES OF INDIA
https://blogs.timesofindia.indiatimes.com/Outraged/had-it-up-to-here-with-hackers/
-
Total Security Daily Advisor
https://totalsecuritydailyadvisor.blr.com/emerging-issues-in-security/novel-attack-allows-internal-threat-actors-access-password-using-thermal-imaging/
-
ITWire
https://www.itwire.com/security/83527-researchers-use-thermail-imaging-to-guess-passwords-from-keyboards.html
https://www.blackhat.com/latestintel/03152019-dont-miss-intriguing-black-hat-asia-briefings.html
https://www.heise.de/security/meldung/Seitenkanalattacken-Passwort-Klau-mittels-Waermebildkamera-und-Tippgeraeusch-4357232.html
https://www.golem.de/news/acutherm-mit-waermebildkamera-und-mikrofon-das-passwort-erraten-1904-140396.html
https://redfoxnews.us/dont-miss-these-intriguing-black-hat-asia-briefings/
https://www.darkreading.com/black-hat/dont-miss-these-intriguing-black-hat-asia-briefings/d/d-id/1334170
https://www.ics.uci.edu/community/news/view_news?id=1388
http://www.cs.uci.edu/ics-researchers-introduce-thermanator-revealing-a-new-threat-to-using-keyboards-to-enter-passwords-and-other-sensitive-information/
https://www.schneier.com/blog/archives/2018/07/recovering_keyb.html
https://www.thetimes.co.uk/article/thermal-imaging-lets-hackers-read-what-you-ve-typed-cxmqtt3rm
http://www.dailymail.co.uk/sciencetech/article-5925865/Criminals-steal-bank-details-recording-HEAT-left-keyboard-fingers.html
https://www.bleepingcomputer.com/news/security/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards/
https://www.mirror.co.uk/tech/hackers-can-steal-your-computer-12858680
https://securityboulevard.com/2018/07/thermanator-attack-uses-thermal-residue-from-keyboards-to-steal-your-passwords/
https://securityboulevard.com/2018/07/recovering-keyboard-inputs-through-thermal-imaging/
https://www.techradar.com/news/creative-keyboard-attack-allows-passwords-to-be-stolen-using-the-heat-from-your-fingers
https://gizmodo.com/scientists-discover-hottest-most-improbable-way-to-ste-1827396066
https://www.zdnet.com/article/this-attack-steals-your-passwords-by-reading-keyboard-heat/
http://www.kswo.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
https://www.techrepublic.com/article/how-hackers-can-steal-your-password-with-an-infrared-photo-of-your-keyboard/
https://www.storypick.com/thermanator-cyber-attack-fingertips//
https://gbhackers.com/thermanator-attack-password-keyboards/
https://fossbytes.com/keyboard-attack-thermanator-steal-password-using-body-heat/
https://www.welivesecurity.com/2018/07/06/thermanator-attackers-heat-keyboard-password/
https://cyware.com/news/thermanator-hackers-could-steal-passwords-by-analyzing-thermal-residue-on-keyboards-df15f4c5
http://www.wfmj.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
https://threatbrief.com/this-keyboard-attack-steals-passwords-by-reading-heat-from-your-fingers/
http://www.wlox.com/story/38581557/your-body-heat-can-help-attackers-steal-your-password-in-new-attack
https://mycomputerlessons.com/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards/
http://hackwolrdwide.com/thermanator-attack-attackers-can-steal-password-and-pins-typed-on-keyboards/tranning-it-hacking/2018/
https://malwaretips.com/threads/thermanator-attack-steals-passwords-by-reading-thermal-residue-on-keyboards-up-to-one-minute-after-input.84900/
https://sensorstechforum.com/thermanator-thermal-residue-passwords/
https://warehousediscounts.co.uk/2018/07/this-keyboard-attack-steals-passwords-by-reading-heat-from-your-fingers/
https://www.journalposts.com/new-insider-attack-steals-passwords-by-reading-thermal-energy-from-keyboards/
https://en.mogaznews.com/Technology/958064/Criminals-can-steal-your-bank-details-by-recording-the-HEAT-left-on-a-keyboard-.html
https://lenta.ru/news/2018/07/05/fingers/
https://www.rtl.fr/actu/futur/il-est-possible-de-voler-un-mot-de-passe-en-filmant-un-clavier-avec-une-camera-thermique-7794077571
https://traders-union.ru/iaftnews/kriptorinok/news/327373/
https://blogs.timesofindia.indiatimes.com/Outraged/had-it-up-to-here-with-hackers/
https://totalsecuritydailyadvisor.blr.com/emerging-issues-in-security/novel-attack-allows-internal-threat-actors-access-password-using-thermal-imaging/
https://www.itwire.com/security/83527-researchers-use-thermail-imaging-to-guess-passwords-from-keyboards.html