Secure
Group Services for Storage Area Networks
|

|
|
Continued
growth and popularity of the Internet fuels
increased reliance on e-business which often
involves data-intensive applications. Consequently,
the amount of information that needs to
be stored and managed can become quite intimidating.
Traditional centralized storage servers, which
have been the workhorses of the industry, are
often unable to meet the storage needs of large
organizations. To this end, they are being replaced
by network attached disks and, more recently,
by Storage Area Networks (SAN-s). A SAN represents a
scalable and reliable storage network that enables efficient
any-to-any connectivity between hosts and storage
devices and provides improved overall resource
utilization. Therefore, SAN-s indeed signify
a major step in the evolution of network storage.
A critical requirement in such a distributed storage
system is the security and integrity of stored
data. Although this problem has been studied
intensively in the past, certain unique features
of the SAN setting result in some new security
challenges. In this project, we concentrate
on safeguarding data (stored on a SAN) from
various threats and attacks with the further
emphasis on efficient key management.
|
|
|

|
|
The goal of the project is twofold:
- to
provide a security architecture for
preserving privacy and integrity of
SAN data.
- to
provide efficient key management solutions
System
Model:
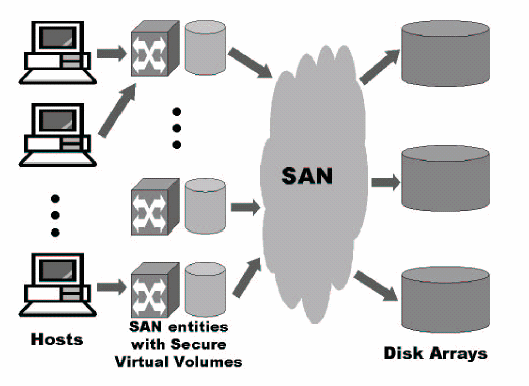
A Storage
Area Network, as seen from the perspective of
a host or a disk, is a network infrastructure
that forwards, in an efficient and reliable
way, both data blocks and commands. The SAN
infrastructure is essentially a collection of
network devices such as high-end switches for
IP or Fibre Channel networks or storage routers.
We use the term SAN entities to refer to these
network devices.
In most SAN
frameworks the actual data owner can control,
fully or in part, the SAN administration. This
is the case in a typical enterprise scenario
as well as in the Storage Service Provider (SSP)
model (where SSP companies sell storage as a
service to their customers). The fact that the
data owner controls the SAN enables the powerful
concept of virtualization for data security.
We utilize these entities to actively
enforce data security policies.
The notable
features of our approach are as follows:
- We delegate
the bulk of the cryptographic operations
to the SAN entities essentially freeing
the hosts from the cryptographic burden.
A host only needs to establish a secure
link with the SAN perimeter. Thus, the level
of user inconvenience introduced by our
system is minimal.
- Since
SAN entities are entrusted with the cryptographic
duties, key management only involves these
(relatively) few entities, as opposed to
involving all possible hosts in the system.
- We recognize
the peer nature of the SAN entities that
are authorized to virtualize a secure volume.
Exploiting this feature, we propose two
different key management approaches: one
based on a simple Public Key Infrastructure
(PKI). The second approach is based on peer
group key agreement techniques.
|
|

 Gene
Tsudik, Project Leader, UC Irvine
Gene
Tsudik, Project Leader, UC Irvine
 Fabio
Maino, Research Collaborator, Andiamo
Systems
Fabio
Maino, Research Collaborator, Andiamo
Systems
 Yongdae
Kim, Research Collaborator, UMinn,
Twin Cities
Yongdae
Kim, Research Collaborator, UMinn,
Twin Cities
 Maithili
Narasimha, Graduate Student Researcher,
UC Irvine
Maithili
Narasimha, Graduate Student Researcher,
UC Irvine

 Y. Kim, F. Maino, M. Narasimha and G. Tsudik "Secure Group Services for Storage-Area Networks"
Y. Kim, F. Maino, M. Narasimha and G. Tsudik "Secure Group Services for Storage-Area Networks"
2002 IEEE International Workshop on Storage
Security, December 2002. kmnt02.pdf
 SISW 2002, Greenbelt, Maryland, December 2002 pdf
SISW 2002, Greenbelt, Maryland, December 2002 pdf

![]() Gene
Tsudik, Project Leader, UC Irvine
Gene
Tsudik, Project Leader, UC Irvine![]() Fabio
Maino, Research Collaborator, Andiamo
Systems
Fabio
Maino, Research Collaborator, Andiamo
Systems![]() Yongdae
Kim, Research Collaborator, UMinn,
Twin Cities
Yongdae
Kim, Research Collaborator, UMinn,
Twin Cities![]() Maithili
Narasimha, Graduate Student Researcher,
UC Irvine
Maithili
Narasimha, Graduate Student Researcher,
UC Irvine
![]() Y. Kim, F. Maino, M. Narasimha and G. Tsudik "Secure Group Services for Storage-Area Networks"
Y. Kim, F. Maino, M. Narasimha and G. Tsudik "Secure Group Services for Storage-Area Networks"
![]() SISW 2002, Greenbelt, Maryland, December 2002 pdf
SISW 2002, Greenbelt, Maryland, December 2002 pdf