Simple and Flexible Revocation Checking with Privacy
| Overview |
Digital certificates, signed by a certificate authority (CA), bind a public key to an identity string, e.g. the a name of an individual or organization. Digital certificates also contain expiry information that a user checks prior to communication. However, due to various reasons, both malicious and benign, certificates may need to be revoked or terminated prematurely. It is not sufficient just to check if a certificate is expired.
Prior to communication a user must be able to inquire about the status of a certificate to be assured that communication is still secure. This is done by issuing a revocation query to the CA service containing revocation information. However, each time a user issues a revocation query a loss of privacy occurs. Namely, two things can discovered:
- Source of revocation query
- Target of query
We propose a technique, called range queries, that allows users to inquire about the status of a certificate while maintaining their privacy. A distribution center can not determine, with a certain statistical probability, exactly which certificate a user is interested in. Full details are located in our paper which can be downloaded here.
| People |
- Gene Tsudik - Research Professor
- John Solis - Graduate Student
| Publications |
-
Simple and Flexible Revocation Checking with Privacy
Privacy Enhancing Technologies (PET 2006), June 2006 [PDF] , [PS]
| Presentations |
| Implementation & Source Code |
Client:
Begin by downloading the binary or source code. Compile the source code
and execute the client. The following interface will be displayed to the user:
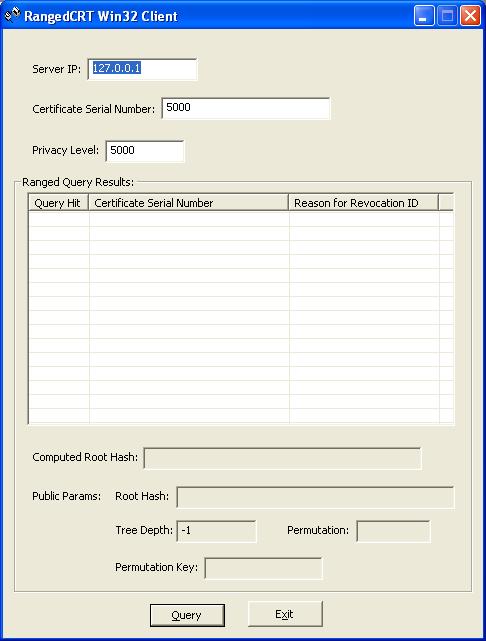
This first interface is the primary interface for the end user. The only editable fields are the first three fields. These include: Server IP Address, Certificate Serial Number, and the desired privacy level (p).
After this information has been entered the user
clicks on the "Query" button and the client attempts to establish a
connection with the server. Once a connection has been established to
the server, the server returns the public parameters of the system, as well
as the results of the client query. An example of these results can be
seen in the following figure:
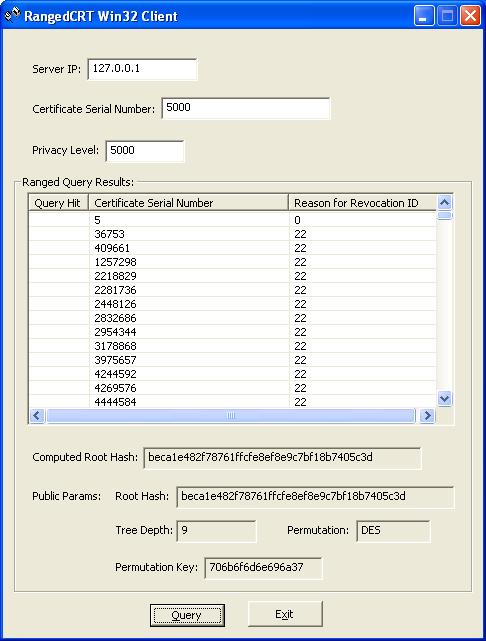
The results from the server are parsed and displayed in the list control for the user. The only field the user is concerned with at this point is the 'Computed Root Hash' field. This value indicates the hash that has been computed from the results returned by the server and the co-path nodes provided by the server. If the computed root hash differs from the publicly signed root hash then the user knows that some tampering of the data has occurred.
Server
The server itself has no interactive interface. All information is provided to the server through a config file that is passed during execution time. This configuration file is a simple text file that has all the information needed by the server. The header information from the a sample (default.conf) file is shown here:
#################################################################################### # Server Configuration File Format # # 1st line: Permutation Algorithm to use: des,rc4,blowfish # 2nd line: Key to use for permutation algorithm # 3rd line: Serial number of smallest possible node value # 4th line: Serial number of largest possible node value # # Remaing lines: #Screen shots:# # ** ReasonID is just a number to be used by administrators and the actual mapping # between ID and a reason is determined by each individual administrator # #################################################################################### des pkomnij7 5 1000000000 36753 22 ./sslcerts/100001.pem 409661 22 ./sslcerts/100002.pem 1257298 22 ./sslcerts/100003.pem 2218829 22 ./sslcerts/100004.pem
Two implementations of the Ranged Query CRT implementation are available for download. The first download is the original Unix implementation which was written in C++ in Slackware Linux 10.0. The second download is a port of the Unix imlementation to the Windows enviornment with both source code and binaries available for download. Both implementations use version 'openssl-0.9.8a' of the OpenSSL library.
Note: All packages require that the OpenSSL libraries be installed and
can be downloaded from the OpenSSL website.
| Linux Source Code | |
| Win32 Source Code | |
| Win32 Binary |