![]()

![]()
Introduction
Dynamic Peer Groups (DPGs) are becoming increasingly popular and ubiquitous. Various peer-to-peer (P2P) systems (e.g. Gnutella, Chord, Pastry) and mobile ad hoc networks (MANETs) are examples of ad hoc groups. These groups are characterized by two important features, (1) lack of trusted authority and (2) dynamic membership, which often implies dynamic topology. These features prompt a number of challenges for routing as well as content placement and retrieval. They also make it difficult to develop effective and efficient security mechanisms.
P2P Systems
MANETs
The need for security in MANETs and P2P has been widely recognized by the research community and the bulk of prior work has been in the context of traditional security services such as access control, secure group communication (group key agreement and key management) and secure routing (in MANETs). Although these services are certainly important, another equally important issue - admission control - has remained mostly out of the spotlight. Informally, it is the problem of group admission, i.e., how one joins an ad hoc group. Only very recently, some work began to make in-roads into this difficult problem.
![]()
Why Admission Control is Necessary?
In general, security services are necessary to provide communication privacy and integrity. These are not possible without secure and efficient key management. Thus, most prior work in peer group security has focused on key management and authentication. However, in DPGs where every user is free to join the group, if anyone is able to obtain the access to the group key, group key management becomes useless. Therefore, mechanisms to control membership are required.
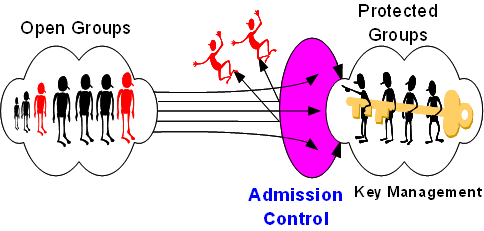
Admission control (aka, membership control or membership management) is needed to allow only authorized users to join the group. This is a very important issue, since all other DPG security services rely upon group membership. In short, group admission control is required to ascertain membership eligibility and to bootstrap other important security services, such as secure group key management and secure routing. Thus, admission control is a prerequisite for group key management.
![]()
Applications
![]() Military Mobile Ad Hoc Networks
Military Mobile Ad Hoc Networks
![]() Private P2P file sharing
Private P2P file sharing
![]() Self-organizing vehicular networks
Self-organizing vehicular networks
![]() Distributed file/storage systems
Distributed file/storage systems
![]() Collaborative workspaces
Collaborative workspaces
![]() Personal area networks
Personal area networks
![]() Home networks
Home networks
![]()
People
![]() Principal Investigator: Dr.
Gene Tsudik
Principal Investigator: Dr.
Gene Tsudik
![]() Graduate Student Researchers
Graduate Student Researchers
![]()
Project Funding
Supported in part by an award from the Army Research Office (ARO) under contract W911NF0410280, in part, NSF awards under 0331707 and 0331690 (ITR-RESCUE), and a grant from SUN Microsystems.
Copyright
2001 (c) SCONCE. All rights reserved.
Best viewed with
Internet Explorer 6.0 & 1024*768 resolution or higher.